Know Can Database Be Fully Secure . The best and easiest way to keep your database secure is to ensure that no one can find it. Sort companies by location, industry, size, valuation & more.
Building With Purpose Built Databases Match Your Workloads To The from image.slidesharecdn.com Your data can be compromised or. Sql server is designed to secure all your data stored in the databases but sometimes we fail to apply the right set of configurations and leave a hole in our system. Also, the simpler its functional structure — the more chances to ensure good protection of each database feature. If you can build in automatic alerting rules, so much the better. However, database server products offer robust security that will help protect your data from unauthorized use. Moreover, it helps in simplifying the management and development of the oracle database in the cloud or traditional deployments. Microsoft's best practices recommend creating a discrete user, either an active directory domain user or group, or a sql server authentication user, to use as the database owner. Consider how your logging data will be secured. If it's all in the application database and that is compromised, an attacker could wipe or falsify the log data.
If it's all in the application database and that is compromised, an attacker could wipe or falsify the log data. Can Database Be Fully Secure Your data can be compromised or. Infrastructure management—including scalability, availability, and security. The rule can open port 1433 for a single ip address or a range of ip addresses. This article suggests a list with the top 10 security considerations based on which you can efficiently secure your sql server instances. Also, the simpler its functional structure — the more chances to ensure good protection of each database feature. This post shows how to manage the dbo, or database. Principals and database object security principals are the individuals, groups, and processes granted access to sql server. These are the default rules that disable read and write access to your database by users. Children's database can never be fully secure the government has agreed to accept the recommendations of a deloitte report which has called into question the security aspects of the contactpoint. Moreover, it helps in simplifying the management and development of the oracle database in the cloud or traditional deployments. Improved security no database can be made completely secure. Logs can contain sensitive information, so aim to minimise this and secure your log data stores. See what you can research. The database management system (dbms) is the software that interacts with end users, applications, and the database itself to capture and analyze the data. Get data and information on 3 million+ companies: If user authentication is managed by the database, then security administrators should develop a password security policy to maintain database access security. Sql developer offers secure connection capabilities with many database technologies. Consider how your logging data will be secured.
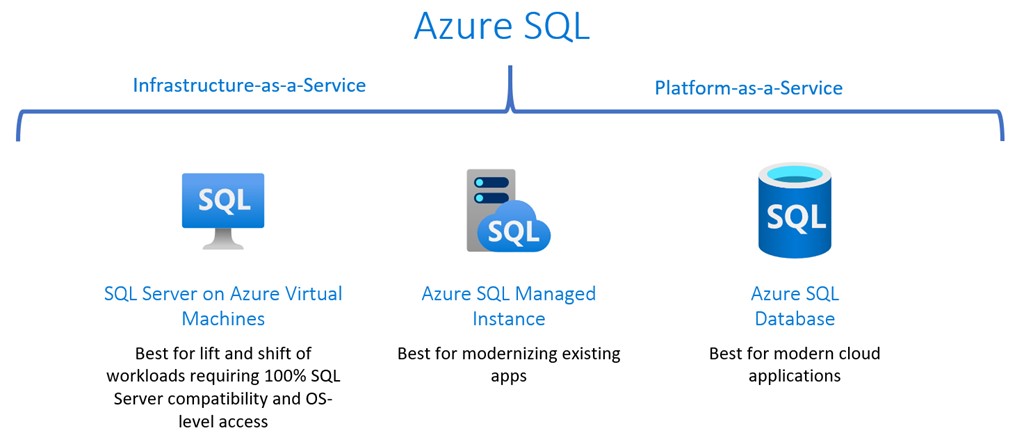
Comparisson Between Sql Services On Azure from www.sqltreeo.com
Given that most people don't manually log into a database all that often, use a password. This article will focus primarily on confidentiality since it's the element that's compromised in most data breaches. If it's all in the application database and that is compromised, an attacker could wipe or falsify the log data. Principals and database object security principals are the individuals, groups, and processes granted access to sql server. It provides vast flexibility and a great variety of tools that can be leveraged for any purpose. Types of databases on azure. For example, database users must change their passwords at regular intervals. Sql developer offers secure connection capabilities with many database technologies. On the overview page, select set server firewall.the firewall settings page for the server opens. Securables are the server, database, and objects the database contains. Improved security no database can be made completely secure.
Infrastructure management—including scalability, availability, and security. Source: www.adamenfroy.com The best and easiest way to keep your database secure is to ensure that no one can find it.
Logs can contain sensitive information, so aim to minimise this and secure your log data stores. As mentioned in step one, database servers typically only have another server (or several) connecting to it. By default, the database cannot be accessed remotely. Each has a set of permissions that can be configured to help reduce the sql server surface area. Amazon relational database service (amazon rds) makes it easy to set up, operate, and scale a relational database in the cloud. For example, database users must change their passwords at regular intervals. As the complexity of application increases, the need for a stronger and secure database emerges. With these rules, you can only access the database through the firebase console. By forcing a user to modify passwords, unauthorized database access can be reduced. However, users can whitelist ip addresses to set up secure database remote access.
Consider how your logging data will be secured. Source: storage.googleapis.com Accelerate your application development in the only cloud with evergreen sql using the latest sql server capabilities , and never worry about updates, upgrades, or end of support again.
Given that most people don't manually log into a database all that often, use a password. Each has a set of permissions that can be configured to help reduce the sql server surface area. Improved security no database can be made completely secure. Children's database can never be fully secure the government has agreed to accept the recommendations of a deloitte report which has called into question the security aspects of the contactpoint. Securables are the server, database, and objects the database contains. Hackers and unauthorized aliens might use these loopholes to penetrate your system. Also, the simpler its functional structure — the more chances to ensure good protection of each database feature. Logs can contain sensitive information, so aim to minimise this and secure your log data stores. It's important for all your database users to use strong passwords. For example, database users must change their passwords at regular intervals.
Microsoft's best practices recommend creating a discrete user, either an active directory domain user or group, or a sql server authentication user, to use as the database owner. Source: twilio-cms-prod.s3.amazonaws.com Although having fully patched software does not necessarily mean your server is fully secure, it is still very important to update your operating system and any other software running on it with the latest security patches.
Select ok and close the firewall settings page. Sort companies by location, industry, size, valuation & more. Securables are the server, database, and objects the database contains. The database management system (dbms) is the software that interacts with end users, applications, and the database itself to capture and analyze the data. See the updates section at the end of this post for more information. When attackers exploit a vulnerability and gain access to a server or system, the first thing they will try to steal is the databases. Far too often we see database access being placed front and center on the homepage of the employee portal, or even open to access through a link sent via an internal email or message. Your data can be compromised or. Also, the simpler its functional structure — the more chances to ensure good protection of each database feature. As the complexity of application increases, the need for a stronger and secure database emerges.
Database security is also a major worry for any customer. Source: img.alicdn.com When attackers exploit a vulnerability and gain access to a server or system, the first thing they will try to steal is the databases.
It's important for all your database users to use strong passwords. Also, the simpler its functional structure — the more chances to ensure good protection of each database feature. The rule can open port 1433 for a single ip address or a range of ip addresses. Moreover, it helps in simplifying the management and development of the oracle database in the cloud or traditional deployments. See what you can research. Improved security no database can be made completely secure. Infrastructure management—including scalability, availability, and security. To do so, run the undopwd.sql script. With these rules, you can only access the database through the firebase console. Install all security patches on time.
Securing the physical environment of your database server is crucial. Source: If your applications use the default password security settings from oracle database 10 g release 2 (10.2), then you can revert to these settings until you modify them to use the release 11 g password security settings.
Given that most people don't manually log into a database all that often, use a password. Securing the physical environment of your database server is crucial. Securables are the server, database, and objects the database contains. These are the default rules that disable read and write access to your database by users. If user authentication is managed by the database, then security administrators should develop a password security policy to maintain database access security. Infrastructure management—including scalability, availability, and security. See what you can research. As mentioned in step one, database servers typically only have another server (or several) connecting to it. However, database server products offer robust security that will help protect your data from unauthorized use. This post shows how to manage the dbo, or database.
Amazon relational database service (amazon rds) makes it easy to set up, operate, and scale a relational database in the cloud. Source: support.kaspersky.com Accelerate your application development in the only cloud with evergreen sql using the latest sql server capabilities , and never worry about updates, upgrades, or end of support again.
Securables are the server, database, and objects the database contains. Although having fully patched software does not necessarily mean your server is fully secure, it is still very important to update your operating system and any other software running on it with the latest security patches. You can now connect to any database in the server with the. The rule can open port 1433 for a single ip address or a range of ip addresses. Given that most people don't manually log into a database all that often, use a password. Logs can contain sensitive information, so aim to minimise this and secure your log data stores. Hackers and unauthorized aliens might use these loopholes to penetrate your system. Failure to take this step can allow a compromised database server to compromise the rest of the machine and possibly infiltrate the network. The database management system (dbms) is the software that interacts with end users, applications, and the database itself to capture and analyze the data. Sql developer offers secure connection capabilities with many database technologies.
The best and easiest way to keep your database secure is to ensure that no one can find it. Source: cmsc28productionstorage.blob.core.windows.net Amazon relational database service (amazon rds) makes it easy to set up, operate, and scale a relational database in the cloud.
Each has a set of permissions that can be configured to help reduce the sql server surface area. If you can build in automatic alerting rules, so much the better. If it's all in the application database and that is compromised, an attacker could wipe or falsify the log data. Each has a set of permissions that can be configured to help reduce the sql server surface area. The database management system (dbms) is the software that interacts with end users, applications, and the database itself to capture and analyze the data. Sort companies by location, industry, size, valuation & more. The rule can open port 1433 for a single ip address or a range of ip addresses. Hackers and unauthorized aliens might use these loopholes to penetrate your system. Install all security patches on time. One reality of managing large organizations involves collecting massive amounts of sensitive data that is stored and managed in.
If you can build in automatic alerting rules, so much the better. Source: miro.medium.com On the overview page, select set server firewall.the firewall settings page for the server opens.
Consider how your logging data will be secured. It provides vast flexibility and a great variety of tools that can be leveraged for any purpose. However, database server products offer robust security that will help protect your data from unauthorized use. One reality of managing large organizations involves collecting massive amounts of sensitive data that is stored and managed in. If user authentication is managed by the database, then security administrators should develop a password security policy to maintain database access security. Logs can contain sensitive information, so aim to minimise this and secure your log data stores. Children's database can never be fully secure the government has agreed to accept the recommendations of a deloitte report which has called into question the security aspects of the contactpoint. Far too often we see database access being placed front and center on the homepage of the employee portal, or even open to access through a link sent via an internal email or message. Failure to take this step can allow a compromised database server to compromise the rest of the machine and possibly infiltrate the network. Given that most people don't manually log into a database all that often, use a password.
For example, database users must change their passwords at regular intervals. Source: img.alicdn.com Imagine having your sql server instance hardened to the maximum security level but leaving the physical location of.

Post a Comment for "Know Can Database Be Fully Secure"